Steemit Won, Anoonies: "That's Fake Vote", Here's the Review!
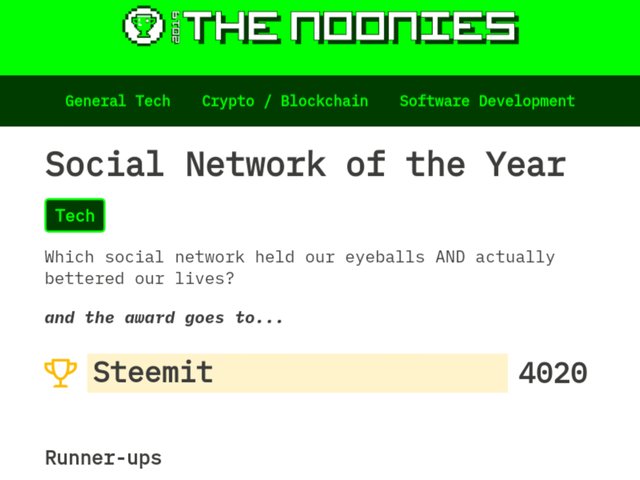
image by screenshot
Hello Steem Community, voting (voting) on the hackernoon.com site has been completed. In this annual contest, noonies.hackernoon.com has announced STEEMIT as the winner for the "Social Network of the Year" category. It seems that what the Steem community has done has succeeded, and that is thanks to everyone's work.
This success is inseparable from the participation of the entire Steem community who have campaigned through their posts to attract as many people as possible. The results were quite satisfying, STEEMIT won. This success is certainly something to be very proud of for all of us. The simple work that we do, ultimately can have a wider impact for the future of the Steem Blockchain.
How not, this vote has shown how users have considerable attention to Steemit. In fact, STEEMIT has removed some other social media, they are the social media most widely used by the public, such as Facebook, Whatsapp, Mesenger and Instagram. We are not sure how that happened. But, the fact is STEEMIT wins.
Their website announced that Steemit received 4020 voters from 8681 voters. The other runner-up positions consist of Gab with the acquisition of 2903 voters and followed by Narrative with the acquisition of 1043 voters. However, unfortunately their site claims that this victory occurred through "Fake Vote".
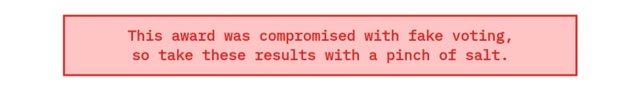
image by screenshot
This award was compromised with fake voting,
so take these results with a pinch of salt.
As you can see above, this red information is posted at the top of the website panel that shows a description of the vote. I do not understand how they can claim it as "Fake Vote".
In the following we will reveal a few things about this, pay attention and give your response!

image source
Introduce Anoonies
Anoonies is Technology Industry Environmentally Friendly Award. Welcome to Hackernoon's First Annual Noonies - where everything is democratic and your voice is the only thing that matters. Choose as many awards as you want. You only get one vote per award. [1]
image source
How Does Voting Work?
We realize that voting can only be done once through any device used by voters. Every voting is registered with the IP ID of the voter. So, one device can only do one vote.

image source
Possible Voter Using VPN?
Some people are at odds with this announcement. Some of us will certainly claim that this is an absolute victory. However, there are some allegations that some voters might use VPN to vote. By using VPN, device users can replace IP ID in a trace manner. So that voting can be done up to several times through the same device.

image source
What is VPN?
VPN (Virtual private network) expands private networks to public networks, and provides the ability for users to send and receive data along public or shared networks as if the user's computer is connected in a private network. Applications that run across a VPN can take advantage of the functions, security, and management of private networks. [2]
Virtual Network, can be interpreted as a network that occurs only applies virtual. There is no network connection between the 2 points that will be connected.
Private, can be interpreted as a network formed by the private sector where not everyone can access it. Encrypted data released remains confidential via the public network. [3]
VPN are created by making virtual point-to-point connections through the use of special circuits or by tunneling protocols through existing networks. VPN that are available from the public Internet can provide several benefits of wide area networks (WAN). From a user perspective, resources available in private networks can be accessed remotely.
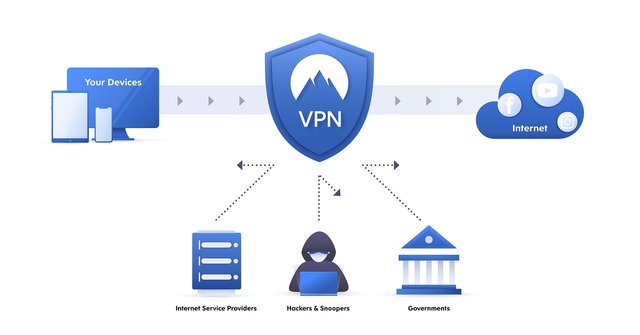
image source
How Does a VPN Work?
VPN requires a server that functions as a liaison between PCs, this VPN Server can consist of a computer with a VPN Server or Router application, for example MikroTik RB 750. To start a connection, a computer with a VPN application Client contacts the VPN Server, the VPN Server then starts using the user name and password and successfully approved VPN Server gives a new IP address to the client computer and then a connection / tunnel will be established. For the client computer can then be used to access various resources (computer or LAN) needed behind the VPN Server to transfer data, print documents , browsing with a gateway provided from the VPN Server, doing a remote desktop and so on. [4]

image source
Does VPN play a role in Voter?
Possibly VPN can be one of the factors so that this vote is said to be a "fake vote". Please note that VPN can protect the user's real IP by maintaining it and replacing it with the VPN server IP. Simply put, your compilation is connected to a VPN, so your real IP (provided by the ISP) is replaced by one of the VPN server's IP.
For example, your IP is Indonesian IP 36.85.1.79. Then you use an American VPN server and your IP will change to 2,354.452.2. So, you can access blocked sites in Indonesia, and your real IP will also remain anonymous and even ISP can't track you.[5]

image source
Need clarification Award?
Whatever the reason, they certainly need strong evidence of this accusation. With various considerations, I really regret this. Statements like this will certainly invite controversy and ask again how their website system works.
However, whatever it is we cannot also accuse and prejudice the bad things to them. We will wait for clarification about their statement. If you know what really happened please let us know in the comments column.
Did you vote with improper actions?
Are you sure you haven't cheated in any way?
Tell us to find out, we hope that the witness will fix this soon and hope that someone will contact them to provide clarification. Or maybe the red panel will disappear from the website soon, it's more perfect.
As a fan of Steem Blockchain, I would like to thank everyone who participated to voice STEEMIT at the awards contest.
Resource :
- [1] https://noonies.hackernoon.com/
- [2] "Virtual Private Networking: An Overview". Microsoft Technet. 4 September 2001.
- [3] Wikipedia : Mason, Andrew G. (2002). Cisco Secure Virtual Private Network. Cisco Press. p. 7.*
- [4] "How can incorrectly configuring VPN clients lead to a security breach?". SearchEnterpriseWAN. Retrieved 14 August 2018.
- [5] Kelly, Sean (August 2001). "Necessity is the mother of VPN invention". Communication News: 26–28. ISSN 0010-3632. Archived from the original on 17 December 2001.
By @ponpase
Aceh, 08/21/2019
Congratulations to Steemit!
Posted using Partiko Android